You are here
Wildcard Certificate Generation for ASA
With network security today, digital certificate has become commonly deployed in an enterprise environment to secure network access as part of endpoint authentication. Many large enterprises have been building their own Public Key Infrastructure (PKI) and issuing certificates for internal use to save cost. One caveat of this approach is these certificates are not publicly trusted so they still need to obtain 3rd party signed certificates from reputable certificate providers for services that are public-facing where the enterprise does not have control over the endpoints like SSL VPN. Since the certificate providers usually charge by the number of signed certificate, the cost might quickly add up if a large number of certificates are required.
For this reason, many may try to resort to wildcard certificate so a single certificate can be shared among multiple devices. A wildcard certificate, particularly one with CN=*.domain.com, has been very popularly used on web servers. If your organization operates your own public web server infrastructure, you most likely own one already. However, if you try to install it a network device, you may discover it being rejected.
This article will provide a step-by-step guide on how to create a wildcard certificate that you can use on your network devices. Here we will use a Cisco ASA as our example but the certificate should work on other type of devices or even network servers as well. For those that are familiar with the concept of wildcard certificate on Cisco ISE 1.2, this should be nothing new to you except that we will be generating the Certificate Signing Request (CSR) separately using OpenSSL.
Explanation:
The concept is to embed the wildcard hostname under Subject Alternative Name (SAN) of type DNS instead of using it in the subject name, while the subject name can be anything you like as long as the identical name also appears under SAN as shown below. Note that the subject name does not need to match any of the URL that you will use this certificate with.
<Subject Name> can be anything (eg. vpn.yourdomain.com)
SAN must contain
DNS=<Subject Name>
DNS=*.yourdomain.com
Our Lab Setup
- OpenSSL (Windows version)
- Windows 2008 CA
- Cisco ASA
Here we assume that the OpenSSL is installed under C:\ drive
Steps
1. Modify the OpenSSL Config File to include SAN attribute.
1.1 Locate [ req ] section and make sure the following is in place
[ req ]
<omitted>
x509_extensions = v3_ca # The extentions to add to the self signed cert
1.2 Locate [ v3_req ] section and add the following line
[ v3_req ]
<omitted>
subjectAltName = @alt_names
1.3 Add the following section at the bottom of the file (should not matter where) and replace them with your desired domain name
[ alt_names ]
DNS.1 = vpn.labminutes.com
DNS.2 = *.labminutes.com
2. Open Widnows CMD and execute the following command to generate a CSR. You may need to run CMD as an administrator
c:\OpenSSL-Win64\bin>openssl req -out lm.csr -new -newkey rsa:2048 -nodes -keyout lm.key
Loading 'screen' into random state - done
Generating a 2048 bit RSA private key
...........................+++
..........................+++
writing new private key to 'lm.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [US]:
State or Province Name (full name) [Some-State]:CA
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Lab Minutes
Organizational Unit Name (eg, section) []:IT
Common Name (e.g. server FQDN or YOUR name) []:vpn.labminutes.com
Email Address []:it@labminutes.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:Cisco123
An optional company name []:
3. Open the lm.csr and you should see a BASE64 output similar to the following. Submit the CSR to your CA.
-----BEGIN CERTIFICATE REQUEST-----
MIIDNDCCAhwCAQAwfDELMAkGA1UEBhMCVVMxCzAJBgNVBAgTAkNBMRQwEgYDVQQK
EwtMYWIgTWludXRlczELMAkGA1UECxMCSVQxGzAZBgNVBAMTEnZwbi5sYWJtaW51
dGVzLmNvbTEgMB4GCSqGSIb3DQEJARYRaXRAbGFibWludXRlcy5jb20wggEiMA0G
CSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDaunq2F1cy7TyGsFyCt+LyNyez39kQ
W5YM3MPqFcdz+B5QByjzXeIfFLpruG8BiyFiRmgTtSeP7hNKn9ijmqxzeTXmUcug
D0BgFb2K8v5QHxMsHFb+CrF3U+nwLZtxANKEfnNKLdLprud2p5AWntyUPV7It3rv
z7Fb3qQmwtSCyCqVeIEgjqowflHrjRZMawixG4oL9PfRy82T3eCb9goxDBze5iKC
w9nriRcGqTR7MlIOT2bpuIqCKeBvKwgx+mlhUUnfLmzU8BcA6hQI4rmDzQoWz6Jo
Q9KzTB1uCO5A79U6RxIV8Vk0ffZhPDhstUNT4QU/qeqN6a+ra9EFxOuxAgMBAAGg
czAXBgkqhkiG9w0BCQcxChMIQ2lzY28xMjMwWAYJKoZIhvcNAQkOMUswSTAJBgNV
HRMEAjAAMAsGA1UdDwQEAwIF4DAvBgNVHREEKDAmghJ2cG4ubGFibWludXRlcy5j
b22CECoubGFibWludXRlcy5jb20wDQYJKoZIhvcNAQEFBQADggEBAFI5Qo+2KuMI
SBiosqJW1uCpxH5FiFhOV39n6SA869+iFL4Au0+Bw45VWoj1B9ezYLRKpxAsfGKe
JiFPdGgawJ23vYO1uycVEtC6rTQf0MJvoASMTNNNEkhrBL74BDRQJBXJrI6ZXKvI
F5WV1luvJVy+HGVJSyTcFRwvucSEBNzi/OeS+Ahzce0ecp+iixvQZEsdqx5CnJGr
PLu5ffxCeLQfPOj3NF5GfB0e/rHrgSRY9+cy7L2ZIqTegj6hoEczZ10aILfEPg/H
ZlRAU1gvKBZ3IpisJHzgZuV2MgJusguf8Z4DQhyiPRJ89jVncj9ccxDEs+PX/WRC
fDsaoVAY6FQ=
-----END CERTIFICATE REQUEST-----
4. Once you have received the signed certificate, open it and verify the Subject Name and SAN.
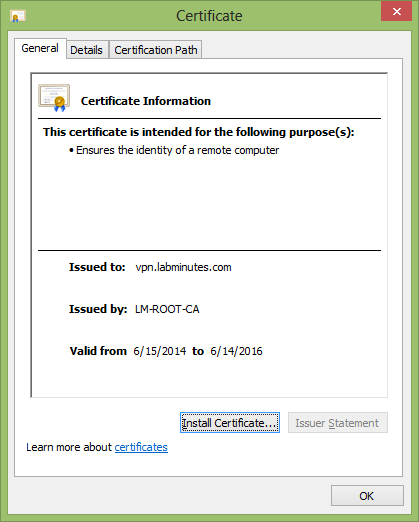
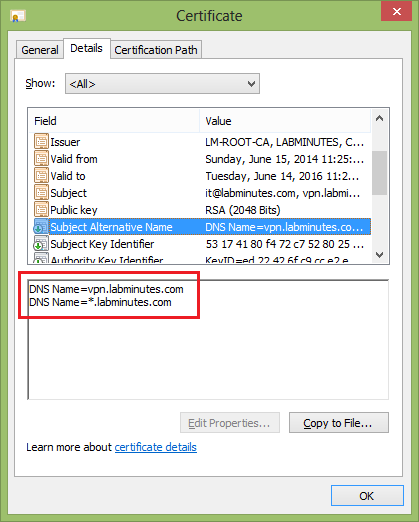
You should now have a private key and certificate files that you can import to your network device/servers. If the device does not accept the key and certificate as separate .pem files but instead combined in a pkcs12 format like the ASA, continue with the following steps.
5. Obtain the root CA certificate and any intermediate certificate from your certificate provider. Concatenate the content of these files into a single file in the following order. Some provider already made this file available known as a certificate chain.
- Intermediate Certificate (BASE64)
- Root Certificate (BASE64)
6. Combine the private key, signed certificate and root CA certificate (chain) into a single pkcs12 file
c:\OpenSSL-Win64\bin>openssl pkcs12 -export -out lm.pfx -inkey lm.key -in lm.cer -certfile lm_root.cer
Loading 'screen' into random state - done
Enter Export Password: Cisco123
Verifying - Enter Export Password: Cisco123
7. Convert the pkcs12 into BASE64 format to be readable by ASA
c:\OpenSSL-Win64\bin> openssl base64 -in lm.pfx -out lm_pkcs12.pem
8. Add the following to the beginning and ending of the pcks12 file
-----BEGIN PKCS12-----
<file content>
-----END PKCS12-----
9. To install the certificate on the ASA, create a CA Trustpoint and import pkcs12 file.
FW1(config)# crypto ca trustpoint CA
FW1(config)# cry ca import CA pkcs12 Cisco123
Enter the base 64 encoded pkcs12.
End with the word "quit" on a line by itself:
-----BEGIN PKCS12-----
MIIPeQIBAzCCDz8GCSqGSIb3DQEHAaCCDzAEgg8sMIIPKDCCCd8GCSqGSIb3DQEH
BqCCCdAwggnMAgEAMIIJxQYJKoZIhvcNAQcBMBwGCiqGSIb3DQEMAQYwDgQIfm6V
j6cG3qQCAggAgIIJmEwIAIbWY318x87jOSPfaMv8yTLzhSVyNIDneP9JUutbL9xL
tq3lQErJpUsGJ+EKwfh43a+FI2uxCrZP2npRRytcAgstlu6eVy0aEd74pMD/5Slv
S9uRRtIsr9M/eQKSkQUHGBGVNH/ki/okndrjh7RgrK4fU00OVuJtPQBeGdn0ybOY
xZDb0ELevmDvh+Tz2Waei5A9Ra9Yiy0qrNvB6x+9H1mZ+b8dSJvSEHm1mS9XJK+S
DK1UjSeq2cqTFG4h8BHOwKp6qCPYBbcxPgRNB5vns3LN4E8/BEAek5BO2nafW7cV
4YrIcU2N1yxDuadwA+pFCT4C2Bc0cHCvSGrhlcZEK6YPQSCq/eALPsxp42zZcmVV
1dRyGBuR3S+3tvYcUMHm9VDpz/7BMOuCY0qhBLvQW9ElJz9x4PZMwDHMmAJVMjmZ
5kHGlZ+SgpuE19N/C2/7/5e0OlZVn5RH50FEAnKjUvdtTb/Ib2iXcw9BrWmzM3iS
HNxsIhY7bSRzCaPyQoyoHpUP3AGZ2yEcnHgcJBiJ8iZxFXAsPFsiV6LRrwPlUlgO
mJn/g3wPLiqvP5MssG7ENL6I2MVcp7NbkxgtO+PMxUh+mbB6j7i/pb35FB4AGQMu
EgO3Iofwhcm+R70mdFFfaNktVvL//j1Dsnt8Enwb2/oUpJt1AMcKTIJfbTBZ4q4G
sSny5v8CWyEcgH7+jFEciHCUucmSKIDxkDivD2NEHhNnW1Z7Z8DlPqrxLHvLty8a
U+8HDIiU88JHQxTGeSshMpbik3sYkCxjovbJOQm6stiFaHlaa2NRohvdGm5PcF6w
sAC5NmX/MAGe6XjuZCYAcSK33TAkI3qvZCxA6MQjc1H2OkjfIIxVQkmzoAzBE12q
PMos/RM1w8iZFQliAmqWbxcNl1eeZt/XhDN+k2QRr1he0rMyNgOGpj6+uAYdzM/9
GkmJpPPwNV9iEe6FRhutlI7/6FyJiEZiEziNXcFuB8R8E53LhTX3CE3C0mxvKNBU
1fE7Pa7wCA48eLVR5HRfM1qexDDbdMaeAuOXGwt09QuiyTOznEi54D8Ex5e0ms95
byQtf8X4TzCCxmO0gTaFfnkGpHMD+YcFag7cKecDRdpUKlijV8aoFheL4+hjMq9K
HJXDc4aQ/Ys916aEOY8/H/A6JC0FW161I2kNtl11pK17g8VSiIdRO4/1AebtRY3/
T31RxbxTsrmXdU7CZlDliMavd6t+qJBJbj01D1Y1Y8aZJq/B4NMPqh0O9x42TkwT
b1pm03hTkOXLG9lqLYOd2FL53ke4ywnnlA10Komgo9V82ExvjswagZDKBpusRoQ4
Aculzd3gmmZU8L4oG6jCOKlHRAgAT2RM07XVRfbO00B3xl3MxybnS2SCkGszUEi9
TRqEN2vckpeQcqpE6iBRxJZAdIYhTaPwTBdXdHlI3+leWzZK0rWBYGDblyaN4HZc
qutt+avBKOUQ7agcDn3WKs7UVEdvLGrS9L6cHvt8I7GWIm70VcZODmnh8Yf0wmd1
K2kJyKF1YKo/3fkRA3KAtIx5KgKfjINCLAxQbyq+RmnDZFSDxOwX2ox4VOXbHrvI
4Stwc7kQneJOg6fZGKqy9Jj3izXdmGiGWfimPPeGB7WJijO3MV5En0/K9+G5JxGb
NbRhT7QWcZWbuu629UFhvm+MgXsL6GB8x94K2MupVrEztOJt6S7I0+3Wrb56/nSr
PNuN7BHtbx99ITv20E6cz/v/elv1wqyiPxDVXy6r7VLx2NtCtgCqX8wiEZop3nXY
Zppp4E/OayRAhTB/ULMv+kShKBdapZqy8P914vidd/u0cxGXI8IO01Er854hwkKh
jdBFbt/B/iZ/2B5ljhffkfPjdFKHlKAo4z2N41KyKk9HwXVwwZ8T4n0nn0cPoFcB
oHqTk4D7XWmS0q9uB/YcCDJ0wVS6PopIyeqk5UWVDg84M0LPwqWF1jD2BVQY3Eau
RyGggYC/nivnhykcnwXt5ObUFeu4kCh/8z/JCMY1kCWwltFI76C0vRX50Jv5wFQd
OH4oz3ZiFrd1sT4abeRilV64KapiLCMjMPfr2LFJAEqN+luzzT76rJ4cPuuGfFZ9
ZD6j51+8JmlsXOr4UjwMfmjD5jj20Z/QqQRbULAOGFwDdqEUo0yxN4EQynFLmAer
RQ7MbUa0HVQ8Jj768fqqRbEXQIVBC1JnNnqxWHMF3jHcXpDZC0Lqrm22Aoy3rF/r
ka76dkuxhYS9e7NC16pEtxVi4TgEd5Ztp3xB7MhAf6wa/Ali7srzK+EnsMtOJAKD
HPXYRSPCXkwpnvuq/G2XmaZsc349waiwH1lYf1wH6PbNpRXexUBzwTJFDhezfaqk
oyWtw5aXlQ6uOmrKQMocNLZFizCLpAm6xRateoTuhJv5/aAbG/zkM+TqfJXf20In
nqsxxsX4RcptJB/J6+TOwfotHrjfBSA+25EpG85mdgVQnraeVXlNBBEhqZJU9Kmn
jWj2bKyzPv0u/GBlkyl/u8Y2h5X4zoiOrEFlrgNl8p6+a4V3nr3n5Gq7GMRZTz2D
h7bWD+BLUiV9aF16jl6RPTU96fb4Ij+moqKk9rGhETL86BlWJgdH6Ot5JV0NVWlO
It05iO2HOEf03RVrWVPq4VmiZihPU3Z+f/3GM5PuXWGV1dIm81w//vzt++JEzlp7
5WkHwvZRpATuXZLxaQpjb39YvY7hB/CIMLjw/p5jPueL3mIJL3awxKJdvlh5or+c
nxOgvPmXKfZu24X80Ip93rjx2ygL1XtQOMy65BGKFpxapsSLzAAoIVtTNCRD3Um+
2puWTvCHwcXLYny29zz9ELg4ljrAczAmn0NTJMWPjJDUrrM5ROekpS3S1omkaCSv
1TrOj0rboPkaDFvY7JPrSJOcbF1DMLYBGqSnO+v2/YgM+KikFoBVNZyezX2XPC3M
6yUNRvWiP+BoePlYpEOJ0hekv1J8sM0MHXzebL3sgDc76w6+cB40F93Vqn9tNnsp
178JUIDmpzw/WrEnZ7pH1QiNd4FGM/cqpq7aTDXZxwRi5B4f3k6QcL1A0Nt/DOy9
Rymbjal6hfOfLU/dkhBMum3LOuSwxkPzFH1iHqveK1BgjcXhwplVDHX1n6/v1Yff
o6Af0FltLjBGaY6jjtcUCkMhFr8AmBnUoUHJI57UG6Q/IRsBZEdhxMKoVqd6QJQH
HFFc5hwhmF5Wx4cmmhD7hwxyKMLM2r8fBptoctaZB2chkWR3IQJmsvSIJZCzYg3c
ivpSuweR4eTpjzcSGCnj/RAnH7EUMIIFQQYJKoZIhvcNAQcBoIIFMgSCBS4wggUq
MIIFJgYLKoZIhvcNAQwKAQKgggTuMIIE6jAcBgoqhkiG9w0BDAEDMA4ECCfKWnrK
Lmw5AgIIAASCBMh2+F4eUvx+k1EghmtJWwfEM7K2pAyR7MelkTI9dkNriixIK8rp
tNgaqFvEqv2yPZCscIJL+9foMXzslM9pGWxRoph7xq31xV6IPJl07tD7ktyvrrVA
yl1J+l6aSxzCY/eCmYKV8mbmdxJsjkFZL+L3SNe38i1RZ/P95kZFV5w8JOHztsnj
kR4NfQFsSmEGjGBoW17LTPeEtG+MM37PRowAA0mOeX42iPeS9gj/Yhpaoe12pvCx
KFf914gDiIHn+5OJKZfBs0+BWNzf8i3Jc+9X5iJI8auzA5pRA3v8YQzPh9u3NLo2
M/qpJ1+MLy4p5BF4Ak1T6EBHwnnTQKMQs3GR+of2hX/0Z1hbKdhkR0NcQ1Z7ARSh
B06H6e3ScX+0loeJEyGM8erqISAK1CDHaKEAB7lrJvFjfwK1YJhu2tYqpQlKyU9x
KoZJP2Jo0cs7sDhnUhnJI6RHjriNBAi3NCAv8rNR7xH5QTxYThhz9lltikHrV4G5
2B/QRkx2ojnl5xC5flhMdeT2gyAegzmDyr0CALYO1PYbr8qAzt+2E/tUcDBf8zT0
lMcJijLkUK5BIA4zkeEvWRiS/IFPVtsgQLx9Hod34q/sBne0fSKGzFlFxG8GLZry
3RX0tW3Wv7/7j9LYVauv5h2S1LoDctO8VevWNamqgjot4HKnVd7A8NQthCT+y7Z4
vOKDesVBcT81cN2Haq1SKOPT/GUnaJGAQw5B77xS4R6qIE7Nzaa3xs5OVOF6abxJ
wqTm2PxG+9vXrNJ3VP1W6qNPogCCfbEm+TrGkpFyVyX7lfZkRWf05gV7NlkQ5u4V
BMbRItyhqT7e7ymF16rB+EDkMxOWipT3JhgyLki8XQj87waJ9YxqZN5TQ/C9zPAQ
xWS2225ZkeO0LGRwvz8crDy8Sk9bK7j05g2fstzeufwRWXFCOSFa8t56GPAQamMa
5VFj8THcsM5jrYXiTbipKQue150q6Wv8pePESeXwy64LgQsVwTglXVCiMVI2RtAl
HUebidvB/tueps43i/FX15r0T1ZkThp7yQpstYai89Ye8w2lELWaH3OqeZbQpJey
AJYH2AMbw2ux0L5EokA9BHNgvWFdsaE30xGlbRgKraRxpWRieHx5uNF0ELq5cPfM
NrISgV0+K7KUq0IMbFUOjnQ2UdyRqQy1lnP95Re++1XwtApTMadkBbh6FQZ1TFH4
bZAaTa8U3ZgRIoK9dkJT2ZW0MCUjTwLBNRGsFSZB4Crtu3SoaIDBb68I7lLWSzUc
I/wRS4EObg1jUPFJytBpX+oMbVELEYRfhGA+ZPMqYdJRBktUdu4kW9aVGrpfAx9K
WhQbhPtx4eZaf2KvmVmMKyeyJ2hzoeiowBvCCmRIWUtj6eoAL6Nt+RR/YHs+mtj1
awXba9f7XpCuqI7t1TvSc6G1YylQGiUPospW1eGRGOAHGFnnPxdQaavPS4KoZ+b6
aixpr5CQjhSpGv64diwxnkUgWWzDGh2FrFvXKY2iGb6PEcwPEXpDKaNCWz2A1K7O
v+BAgulQfVAVec+JMWAq/UQlRLzYxaU/YWofNBpar1IlqNu4g4M8Mv1aj21Y4H4B
OJVInSDGTIGzhqp2R64eLoJ5g64/jQPc1LGkDK2GS7JpGG8xJTAjBgkqhkiG9w0B
CRUxFgQUc8oXLkBXC4rTP1cXf+/zP5qftjUwMTAhMAkGBSsOAwIaBQAEFLxyHFIY
xdYuU3XTGd/XhQL/+/X3BAjWXPwI6NHjWwICCAA=
-----END PKCS12-----
quit
INFO: Import PKCS12 operation completed successfully
10. Verify that the identity certificate and the associated root certificate are installed
FW1(config)# show crypto ca certificate
CA Certificate
Status: Available
Certificate Serial Number: 6ed879a75e0ff2924a40945fe9a692cd
Certificate Usage: Signature
Public Key Type: RSA (2048 bits)
Signature Algorithm: SHA1 with RSA Encryption
Issuer Name:
cn=LM-ROOT-CA
dc=LABMINUTES
dc=COM
Subject Name:
cn=LM-ROOT-CA
dc=LABMINUTES
dc=COM
Validity Date:
start date: 16:08:17 PST Sep 15 2012
end date: 16:18:16 PST Sep 15 2017
Associated Trustpoints: CA
Certificate
Status: Available
Certificate Serial Number: 611ba0e00000000000af
Certificate Usage: General Purpose
Public Key Type: RSA (2048 bits)
Signature Algorithm: SHA1 with RSA Encryption
Issuer Name:
cn=LM-ROOT-CA
dc=LABMINUTES
dc=COM
Subject Name:
e=it@labminutes.com
cn=vpn.labminutes.com
ou=IT
o=Lab Minutes
st=CA
c=US
CRL Distribution Points:
[1] ldap:///CN=LM-ROOT-CA,CN=LM-WIN2008-DC1,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=LABMINUTES,DC=COM?certificateRevocationList?base?objectClass=cRLDistributionPoint
Validity Date:
start date: 22:25:42 PST Jun 15 2014
end date: 22:25:42 PST Jun 14 2016
Associated Trustpoints: CA
11. Test the certificate with SSL VPN. When you browse to the SSL VPN login page by name, you should not get any certificate warning, assuming that you have the root certificate trusted. Note that the URL (anything.labminutes.com) does not have to match the certificate subject name (vpn.labminutes.com)
FW1(config)# ssl trust-point CA
FW1(config)# webvpn
FW1(config)# enable OUTSIDE
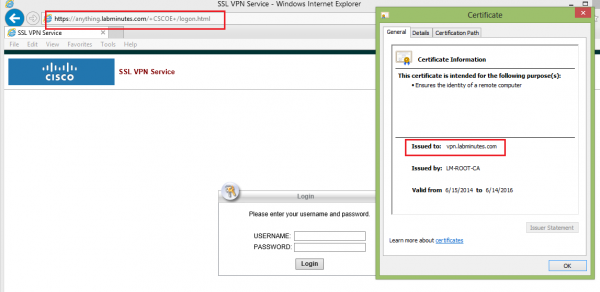
Here are a few things to keep in mind
- Some providers treat a certificate with wildcard in the SAN field the same as a regular wildcard certificate so it may cost more than a regular certificate but this can easily be justified when it is used for multiple network devices and services.
- Sharing the same certificate on multiple devices always lowers the security and increases the chance of the certificate being compromised. A compromised certificate on a single device results in certificates on all other devices having to be reinstalled.
- Even though this method should work on most modern web browsers on majority of device types, you should always test and make sure the target platforms in your deployements are supported.


1 comments
Missing a line
It's missing a line in the openssl.cnf file (at least the one included in Ubuntu 14.10):
[ req ]
<omitted>
req_extensions = v3_req